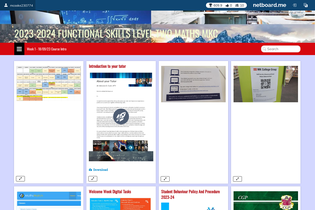
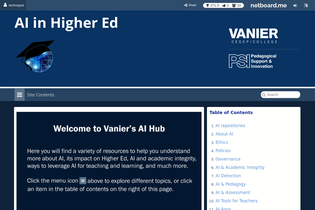
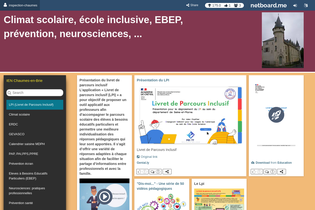
Efficient online teaching tool, offering a streamlined experience for educators and students in the digital learning environment
General workflow:
Register and manage students and other teachers.
No emails required.
Gather and share education materials with your students.
Enable your students to create own pages, vote and comment on liked pages.
Create study groups and publish pages to groups libraries.
Students will see pages published to their groups and will be updated on changes.
Enable collaborative work allowing students to publish own pages to the group.
See how to:
-
Organize different content
Combine images, links, documents, videos and other Web content on the single Web page
-
Edit a page
Organize it in the way you like
-
Personalize a page
Create the theme, using own photos and pictures in the design
-
Add Quizzes
Create quizzes and add them to your pages
Add new content from any web page in a single click using browser extension for Google Chrome or Firefox
Build a trusted environment
Control who can collaborate with your students:
Establish a friendship with other organization accounts to enable students collaboration.
Only friendly organizations teachers and students can collaborate with your students.
Control the level of access for each friendly organization.
Create cross-organizations groups and groups libraries.
Build you own trusted collaboration network.
Our pricing
netboard.me
Choose a subscription plan for netboard.me services
- Unlimited number of netboards
- Try out how the quizzes work
- No ability to upload video or audio
- Sharing private netboards unavailable
- No student accounts included

- Unlimited number of netboards
- Unlimited number of quizzes
- Share your boards privately by using Access Links or by listing users directly
- Includes 40 student accounts to organize a classwork
- Upload video (up to 300Mb) and audio files (all users)
- Group, organize and manage your netboards using collections
- Hide or reveal posts and tabs or schedule them for automatic publishing
- Other users can send you direct messages, with photos, videos, documents and audio
- Accept or reject comments and posts before they are published online
- LMS integration support
- Unlimited number of netboards
- Unlimited number of quizzes
- Share your boards privately by using Access Links or by listing users directly
- Upload video (up to 300Mb) and audio files (all users)
- Group, organize and manage your netboards using collections
- Hide or reveal posts and tabs or schedule them for automatic publishing
- Other users can send you direct messages, with photos, videos, documents and audio
- Accept or reject comments and posts before they are published online
- LMS integration support
Looking for something special? Contact our Sales team and get a quote.
* VAT is not included in the price. It will be calculated depending on your country during checkout.
** You will be charged in your local currency (e.g., Euros, Canadian Dollars, etc.) if supported by our billing provider. In this case you will also be invoiced in your local currency. Start the checkout to see the price in your local currency.